This post will get you started with the Pentest Linux distribution of choice, Kali (now in version 1.1.0 and formerly known as Backtrack). It will furthermore go a little into how the environment can be setup in order to provide anonymity and privacy.
Kali linux is maintained by Offensive Security and is based on a Debian Linux distribution, with a build-in base of approx. 600 various security tool. The distribution can be downloaded from here in various formats.
The easiest way of getting started (assuming a standard Windoze user) is by running it in a virtualized enviroment such as VMware Workstation or similar. Other install methods are also possible, as live USB boot etc. However for the casual user the VM installation should be just fine.
Lots of fine manuals as to get it up and running is available, so go Google it (pretty straightforward). Henceforth it it is assumed that the Kali installation is up and running 🙂
Update to latest and greatest versions
The first thing you will want to do (and do once in a while) is running the following one-liner from console:
apt-get update && apt-get upgrade -y –force-yes && apt-get dist-upgrade -y –force-yes
This will update all the software packets and distribution to the latest and greatest versions.
Anonymity in Kali with TOR
TOR is a anonymous proxy network made freely available by privacy enthusiasts. It is curiously enough also a favorite way of hiding tracks (primary the Pentesters origin) when doing pentesting.
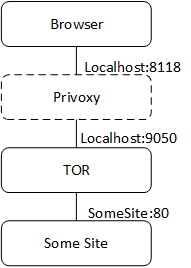
The traffic flow using Privoxy and TOR
TOR is easily installed using the apt package. Simply issue from terminal:
apt-get install tor
The configuration file bundled is good to go for purposes described here, but should the need be to reconfigure the listening port or other config it can be done with:
nano /etc/tor/torrc
TOR is depended on accurate time information. Hence NTP should be updated (particulary if running on a VM installation which has been in hibernation). Run:
service NTP restart
Now the TOR service can then be started with:
service tor start
This will have created a sock5 listener on port 9050, which will forward trafic through the TOR network.
Next step is not necessary, but I usually recommend it. Run the trafic through another scrubber, Privoxy. Again install the program with APT.
apt-get install privoxy
To chain the privoxy trafic through TOR uncomment the 4 lines in the config file:
nano /etc/privoxy/config forward-socks5 / 127.0.0.1:9050 . # # # The public Tor network can’t be used to reach your local network, # if you need to access local servers you therefore might want # to make some exceptions: # forward 192.168.*.*/ . forward 10.*.*.*/ . forward 127.*.*.*/ .
The service is afterwards started with
service privoxy start
Privoxy will by default listen on localhost:8118 as a HTTP proxy. Note that it has to be issued ‘localhost’ and not ‘127.0.0.1’
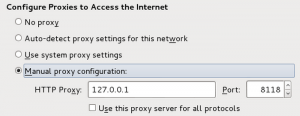
Set the settings of Iceweasel to chain traffic as Browser->privoxy->TOR->someSite
Another little anonymity tip
Proxychains can be used to forward all network traffic from any program (ie. NMAP) through TOR. It is build-in to Kali but has as of current a small defunct. In order to fix it create a symbolic link with
ln -s /usr/lib/proxychains3/proxyresolv /usr/bin/
AND fix the config file with
nano /usr/lib/proxychains3/proxyresolv
so that the line here looks like below export LD_PRELOAD=libproxychains.so.3
now an anonymous nmap scan can be performed like so:
proxychains nmap -sT -PN -n -sV -p 80,443,21,22 1.1.1.1
Adding a secondary browser to Kali
An easy way of adding a secondary browser is the chromium browser. It can be installed with APT with
apt-get install chromium-browser -y
Since this browser will not run as root create a new non-priv user with
adduser -u chrome
and afterwards start the browser with
gksu -u chrome chromium-browser

Be the first to comment on "Anonymity with TOR in KALI"