Installing the FTD 6.2.2 update on a ASA 5515X
I noticed that Cisco released FTD 6.2.2 yesterday (05-sep-2017), why I naturally had to put it in my Demolab right away in order to see if RA-VPN was indeed now included on the ASA platforms. However I quickly bumped into some minor problems… This post reflects some of the experiences I had along the way of getting it working.
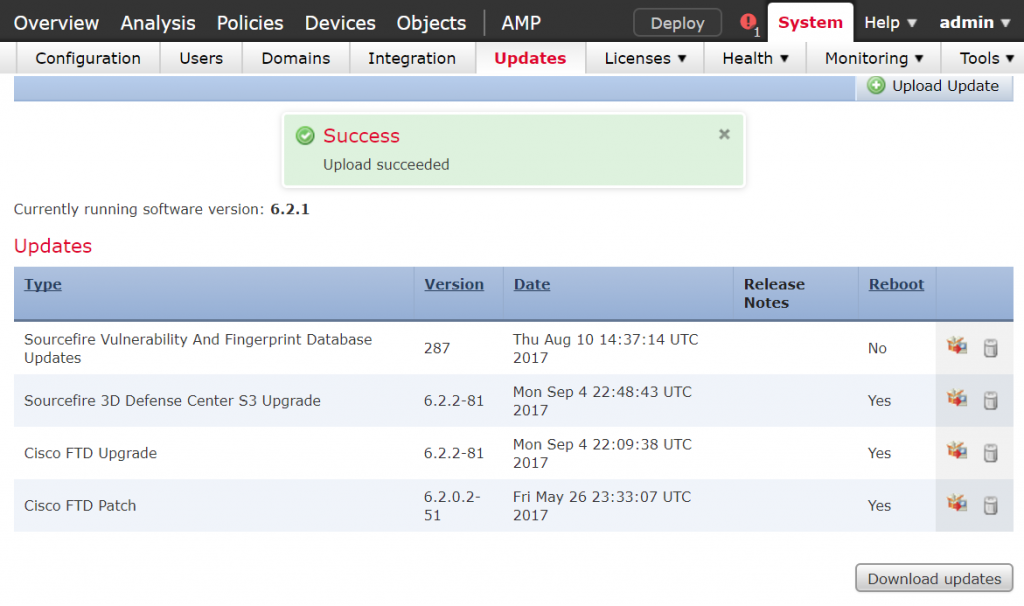
Downloading the Update from Cisco.com and uploading them again onto the FMC is trivial, though I would have liked an direct integration between the FMC and an update service.
Rushing in…
I chose to not read the 6.2.2 release note (shame on me) and went directly onto installing the update on the ASA appliance. The joy of anticipation only lasted a short while as an error message was promptly returned.
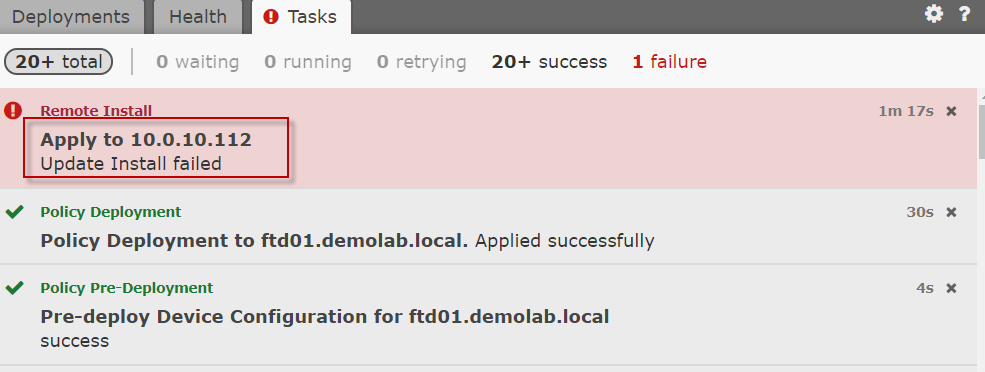
Directly updating the FTD software without any thinking could fail miserably.
Biting the bullet…
I turned to the release note which (unfortunately) quite clearly stated that certain prerequisites had to be meet before updating the software. Note to self.. Always read the manual…
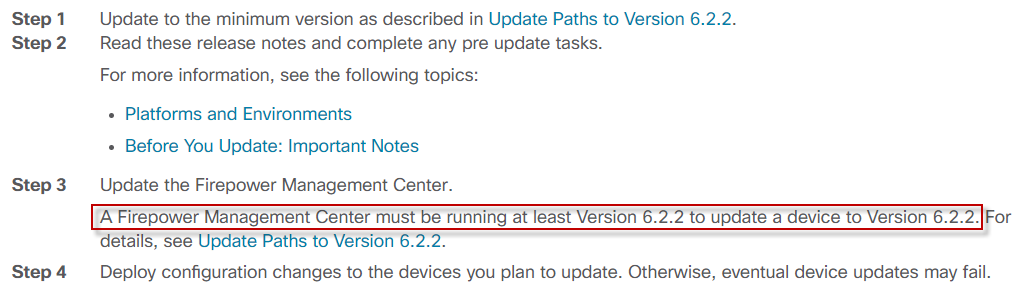
The release note is very specific about requirements for the FTD 6.2.2 update
Quickly checking my versioning (which I of course knew was older) in the GUI did state I was running on 6.2.1.
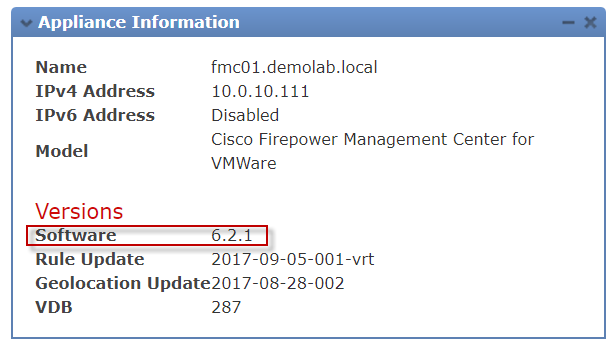
I was only running FMC 6.2.1 in my demolab environment. Time for an upgrade.
Just out of curiosity
Before satisfying the prerequisites I chose to dive a little into troubleshooting, to see how the system logs would tell me of the error and remediation.
I started of by performing an upgrade readiness test on the ASA platform
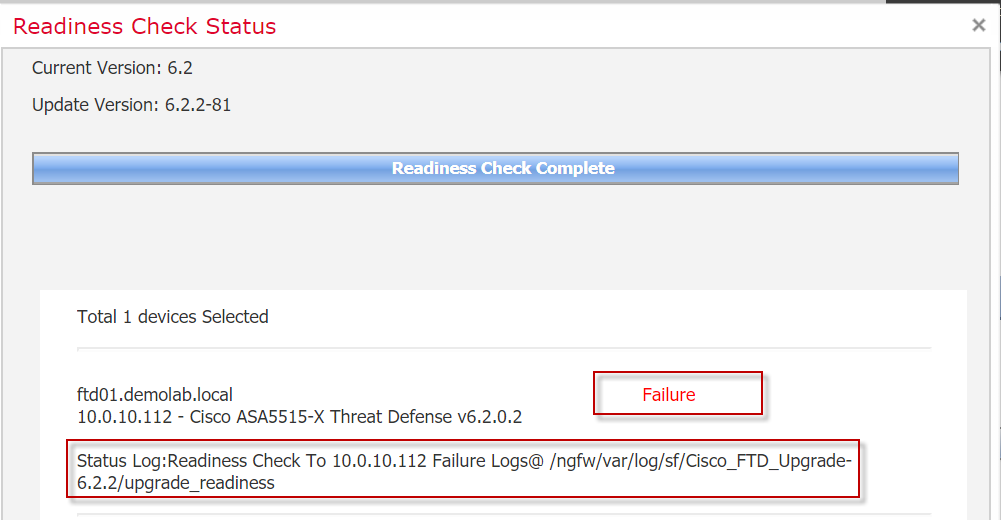
The FTD readiness check throws a failure with a reference to a log file (/ngfw/var/log/sf/Cisco_FTD_Upgrade-6.2.2/upgrade_readiness).
I could have wished for a more complete cause of the upgrade failure directly from the assessment test but OK. It is worth noting that the failure log file being referenced is not located on the FMC but rather on the FTD device.
In order to access the failure log you need to login to the FTD through SSH and run the “Expert” command, which will take you to “linux shell mode”.
> > expert admin@ftd01:~$
From here different logs can be viewed
admin@ftd01:~$ ls -l /ngfw/var/log/sf/Cisco_FTD_Upgrade-6.2.2/upgrade_readiness/ total 16 drwxr-xr-x 2 root root 4096 Sep 6 13:25 000_start drwxr-xr-x 2 root root 4096 Sep 6 13:26 200_pre -rw-r--r-- 1 root root 3114 Sep 6 13:26 flags.conf.complete -rw-r--r-- 1 root root 3675 Sep 6 13:26 main_upgrade_script.log
First diving into the most obvious one
admin@ftd01:~$ more /ngfw/var/log/sf/Cisco_FTD_Upgrade-6.2.2/upgrade_readiness/main_upgrade_script.log [170906 13:24:49] Readiness check for :Cisco_FTD_Upgrade-6.2.2-81 [170906 13:24:49] ##################################### [170906 13:24:49] # UPGRADE READINESS CHECK STARTING [170906 13:24:49] ##################################### [170906 13:24:49] SKIP 000_start/000_check_update.sh [170906 13:24:49] SKIP 000_start/001_configure_bootloader.sh [170906 13:24:49] BEGIN 000_start/100_start_messages.sh [170906 13:24:50] SKIP 000_start/101_AWS_clock_fix.sh [170906 13:24:50] SKIP 000_start/101_run_pruning.pl [170906 13:24:50] BEGIN 000_start/102_check_sru_install_running.pl [170906 13:24:50] BEGIN 000_start/105_check_model_number.sh [170906 13:24:51] SKIP 000_start/106_check_HA_sync.pl [170906 13:24:51] BEGIN 000_start/106_check_HA_updates.pl [170906 13:24:51] BEGIN 000_start/107_version_check.sh [170906 13:24:52] BEGIN 000_start/108_add_index_for_appIdInfo.sh [170906 13:24:52] BEGIN 000_start/108_check_sensors_ver.pl [170906 13:24:53] BEGIN 000_start/109_check_HA_MDC_status.pl [170906 13:24:54] BEGIN 000_start/110_DB_integrity_check.sh [170906 13:25:03] BEGIN 000_start/111_FS_integrity_check.sh [170906 13:25:03] BEGIN 000_start/112_CF_check.sh [170906 13:25:03] BEGIN 000_start/113_EO_integrity_check.pl [170906 13:25:39] SKIP 000_start/125_verify_bundle.sh [170906 13:25:39] SKIP 000_start/170_link_log.sh [170906 13:25:39] BEGIN 000_start/250_check_system_files.sh [170906 13:25:40] SKIP 000_start/320_remove_backups.sh [170906 13:25:40] SKIP 000_start/400_run_troubleshoot.sh [170906 13:25:40] BEGIN 000_start/410_check_disk_space.sh [170906 13:25:43] BEGIN 200_pre/001_check_reg.pl [170906 13:25:44] BEGIN 200_pre/002_check_mounts.sh [170906 13:25:46] BEGIN 200_pre/003_check_health.sh [170906 13:25:48] BEGIN 200_pre/005_check_manager.pl [170906 13:25:49] BEGIN 200_pre/006_check_snort.sh [170906 13:25:52] FAILED 200_pre/006_check_snort.sh [170906 13:25:52] continuing on next script due to readiness check. [170906 13:25:52] BEGIN 200_pre/007_check_sru_install.sh [170906 13:25:54] BEGIN 200_pre/009_check_snort_preproc.sh [170906 13:25:57] BEGIN 200_pre/011_check_self.sh [170906 13:25:59] BEGIN 200_pre/015_verify_rpm.sh [170906 13:26:02] SKIP 200_pre/100_check_dashboards.pl [170906 13:26:02] SKIP 200_pre/100_get_snort_from_dc.pl [170906 13:26:02] BEGIN 200_pre/100_log_version.sh [170906 13:26:02] SKIP 200_pre/101_check_uncommitted_data.pl [170906 13:26:02] SKIP 200_pre/110_setup_upgrade_ui.sh [170906 13:26:02] SKIP 200_pre/120_generate_auth_for_upgrade_ui.pl [170906 13:26:02] SKIP 200_pre/152_save_etc_sf.sh [170906 13:26:02] SKIP 200_pre/168_rm_bad_boot_EFI.sh [170906 13:26:02] SKIP 200_pre/199_before_maintenance_mode.sh [170906 13:26:02] SKIP 200_pre/200_enable_maintenance_mode.pl [170906 13:26:02] SKIP 200_pre/201_disable_faild.sh [170906 13:26:03] SKIP 200_pre/202_disable_syncd.sh [170906 13:26:03] SKIP 200_pre/400_restrict_rpc.sh [170906 13:26:03] SKIP 200_pre/470_revert_prep.sh [170906 13:26:03] SKIP 200_pre/500_stop_system.sh [170906 13:26:03] SKIP 200_pre/501_recovery.sh [170906 13:26:03] SKIP 200_pre/501_stop_blackbird_cards.sh [170906 13:26:03] SKIP 200_pre/600_ftd_onbox_data_export.sh [170906 13:26:03] SKIP 200_pre/610_lamplighter_010_artifacts_export.sh [170906 13:26:03] SKIP 200_pre/999_enable_sync.sh [170906 13:26:03] Readiness check completed.... [170906 13:26:03] Attempting to remove upgrade lock [170906 13:26:03] Success, removed upgrade lock [170906 13:26:03] [170906 13:26:03] ####################################################### [170906 13:26:03] # UPGRADE READINESS CHECK COMPLETE status : FAILED! # [170906 13:26:03] ####################################################### admin@ftd01:~$
Note that the line containing the Snort engine check fails. Diving a little more into this can be done in the check Snort log
admin@ftd01:~$ more /ngfw/var/log/sf/Cisco_FTD_Upgrade-6.2.2/upgrade_readiness/200_pre/006_check_snort.sh.log ********************************************************** [170906 13:25] Starting script: 200_pre/006_check_snort.sh Entering 200_pre/006_check_snort.sh... Snort build is too old. Please apply AC Policy from FMC before attempting upgrade. admin@ftd01:~$
Conclusion is that the FMC version and the Snort engine build seems to be tightly integrated and thus depended. It would be nice with a simple versioning check of the two and easy to grasp error message. But again I could just have read the release notes as I should.
Back to upgrading FMC
Upgrading the FMC is no different from upgrading the FTD on the appliances. However you need to bear in mind the upgrade path.
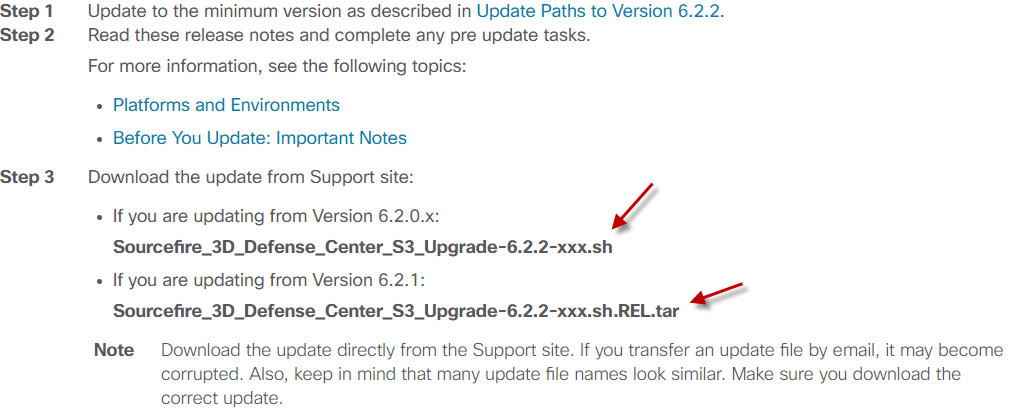
Choose the right FMC upgrade file as referenced in the release note is important.
Be aware though that it might take a short while to perform.
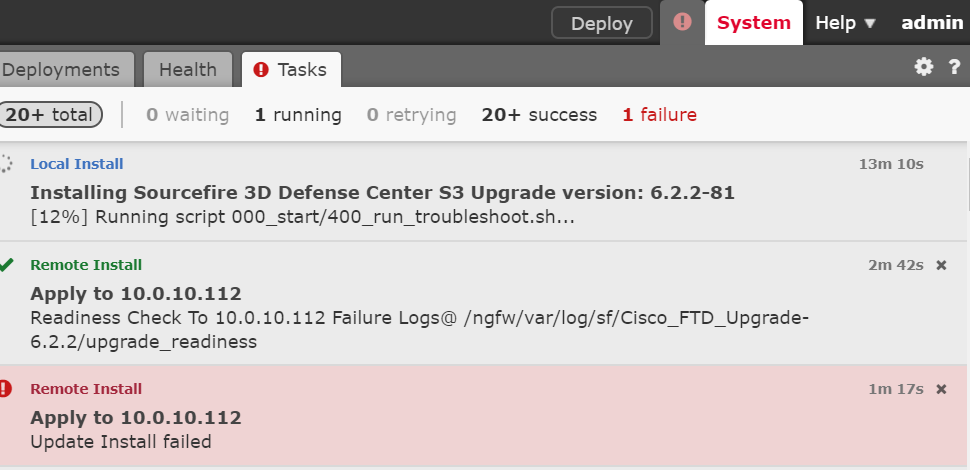
Upgrading the Cisco FMC might take some minutes. It should be noted however that this particular instance is running on a very skinny VMware demolab environment.
When it has completed the first part of the installation and is rebooted the FMC needs to run a series of scripts in order to become operational.
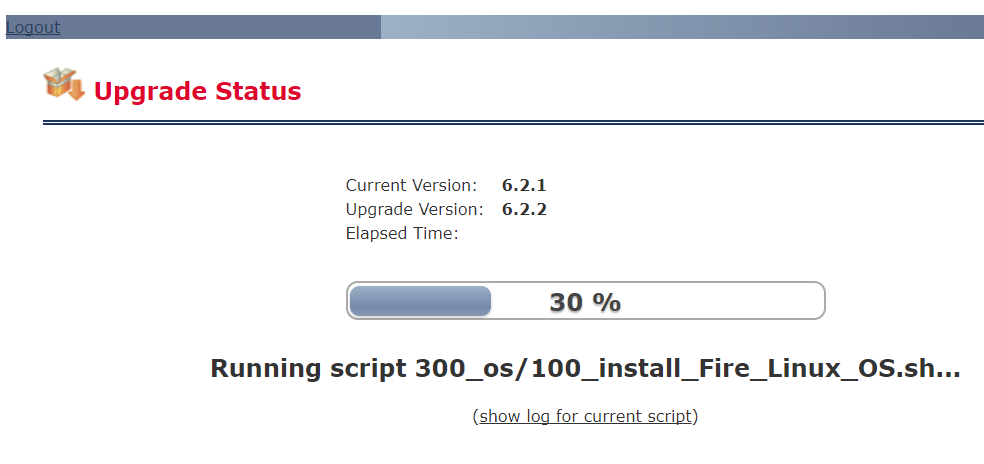
Upon reboot the FMC will run a few script to complete the upgrading process. Patience….
Reaping the rewards 🙂
Immediately the FMC is up an running again you notice a new tab called “Intelligence”. This is where it is possible to include various other IOC threat feeds into the platform through STIX og TAXII. Can’t wait to explore this particular feature. But that will be in a later writing.
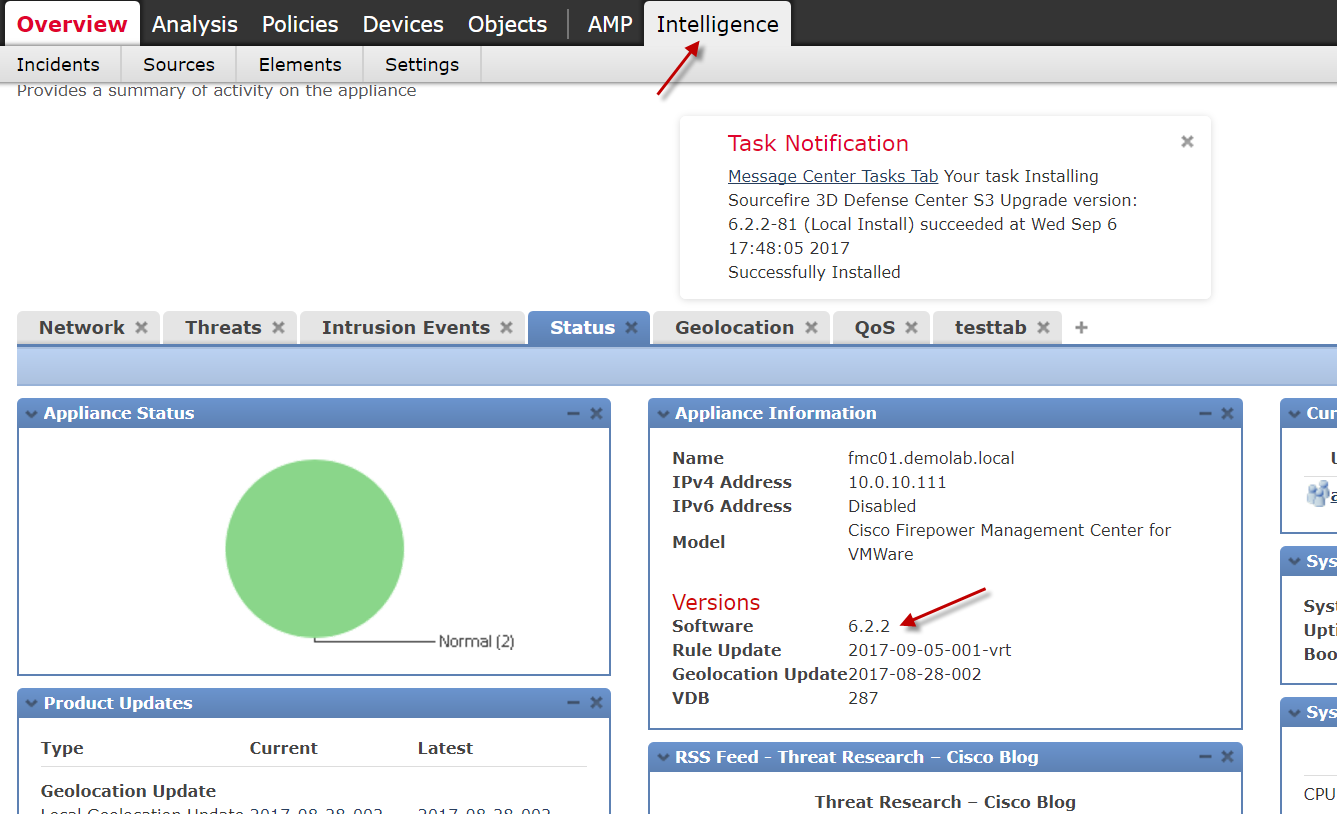
The new ‘Intelligence’ tab of the Cisco FMC. Can’t wait to befriend it 🙂
Still no love
After having become compliant with the FMC version required in the release note, the FTD upgrade was tried again. Unfortunately it failed… again.
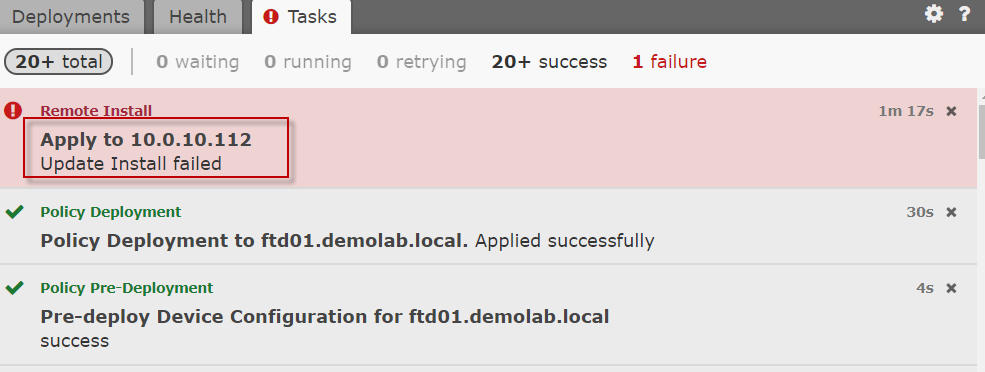
FTD upgrade fails again even through the FMC was upgraded.
Grudgingly I returning to the Release note (see picture way above) step 4 where it does indeed say that you have to deploy your policies before venturing forth…
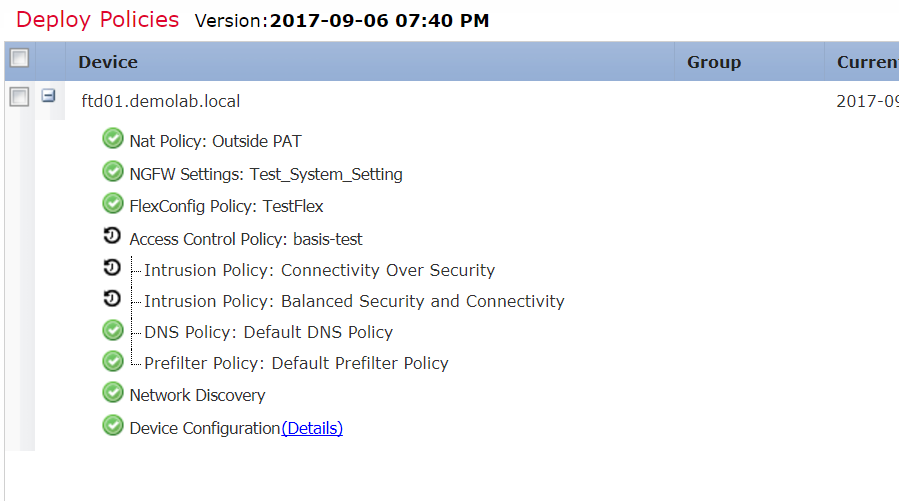
Remember to deploy policies to the FTD before trying to upgrade the FTD. Even if you have not changed anything.
EUREKA!!
Re-deploying the policies did the trick and the software was successfully deployed. And yes it is now possible to add AnyConnect to the ASAs running FTD! 🙂
(edit) It is NOT possible deploying the Anyconnect configuration if the FMC is running in Eval mode!
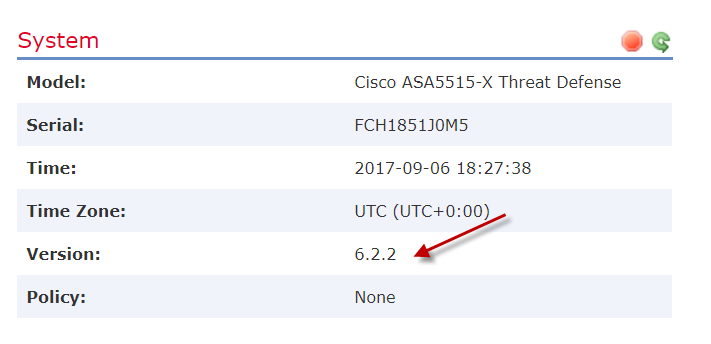
The FTD 6.2.2 was successfully deployed
Note that it took a painfully long install period for the ASA to be successfully upgraded.
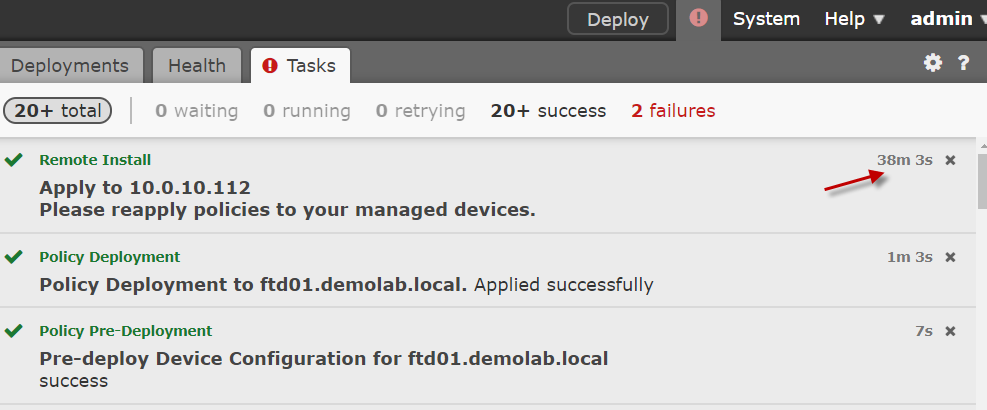
Note that it takes a while for the upgrade to complete
The main take-way from this was the ever-so-cliche saying “Read the #¤!&¤#& Manual”. Coming up next is a more detailed look into the 6.2.2 release.

Don’t be a gunslinger… Read the release note!

I looked all over the web until ran into your post which suggested my upgrade failure might be due to FMC needs to be upgraded before the appliance.
Sadly Cisco support was clueless too…
Thanks for sharing!
I had the same issue when I tried upgrading the FTD from 6.2.3 to 6.4 version without doing the FMC first. The FMC upgrade took about 7 hours total (VM) and once the process was complete, I was able to apply the upgrade to FTDs. Thank you kindly 🙂