There are several ways of authenticating toward the management interface of a Palo Alto Networks Firewall (PANW). The authentications options boils down to three distinct ways namely (or mixes of the three):
- Local Username, Local Password
- Local Username, Remote Password
- Remote Username, Remote Password
For a small deployment with few administrators option #1 i viable through not wildly secure as the on-box password is seldom changed. Better security is obtained in option #2 by linking the local User (The reason for having the local User is in order to provide the assigned roles and privileges) to an external password source (LDAP, RADIUS, TACACS, SAML, Kerberos) as this is often enforced changed at regular intervals. However this scales very poorly when the amount of administrators becomes greater or changes often. For these environments, and as a general best-practice, remote authentication and authorization is preferred which is option #3.
By far the most common way of implementing option #3 is through RADIUS, though TACACS and SAML is also supported for this deployment (but not LDAP). RADIUS authentication can be implemented in many different products which includes a RADIUS server (most often NAC products). Microsoft NPS can be used if cost is paramount but is not very admin friendly and scales poorly if also needed for 802.1x purposes. In this post I will show how to implement it using Cisco Identity Service Engine (ISE) 2.3 as this is a common platform throughout the industry.
Prepping Cisco ISE 2.3
Cisco ISE does not come prepopulated with the necessary RADIUS Vendor Specific Attributes (VSA) required for Palo Alto Networks. These needs to be implemented by hand, either by manually writing the following values into a custom dictionary or by importing the one below I have exported for the same purpose.
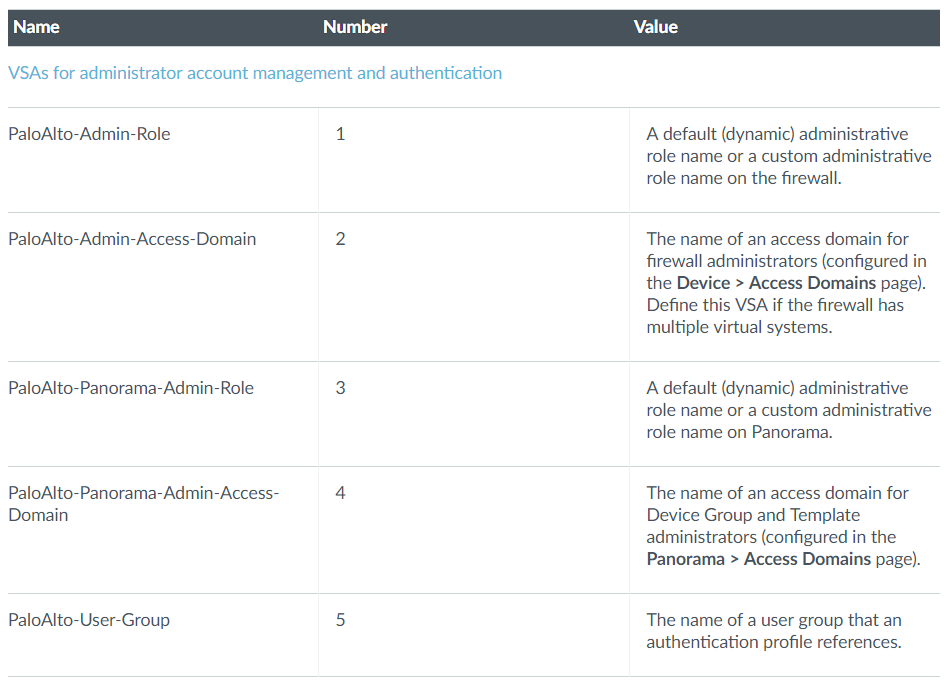
List of relevant PAN-OS 8.0 Authentication VSA can be found in the admin guide or here. Note that only the 5 first are relevant for authentication purposes.
In order for everyone not having to write everything themselves I have Exported the Dictionary from ISE 2.3.0.298 for easily download and import (dictionary.PaloAltoNetworks). It is fairly easy to import the new dictionary as shown below.
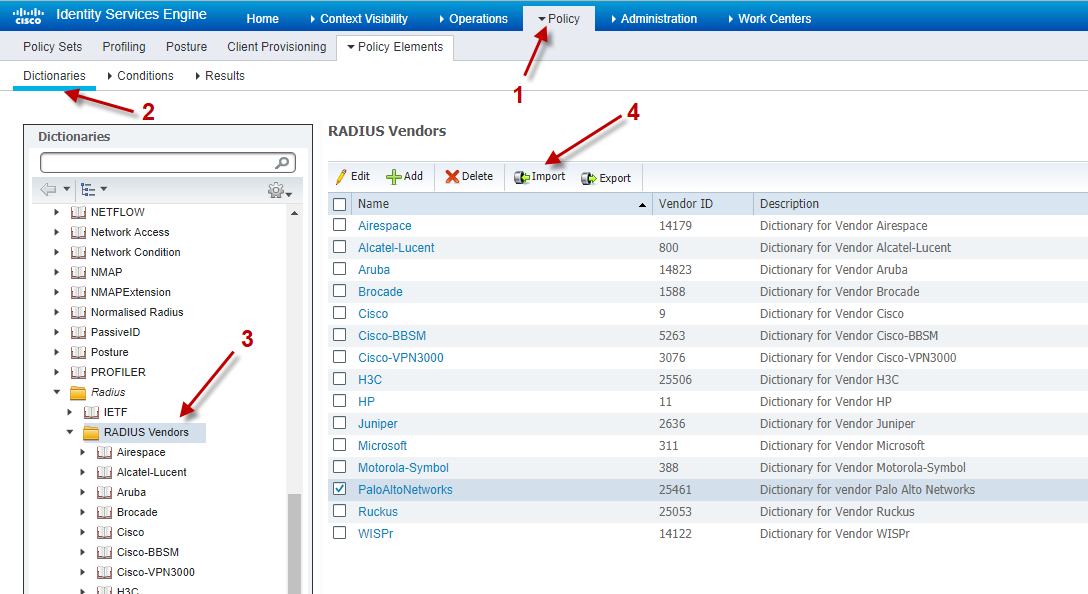
How-to import Palo Alto Networks RADIUS VSA Dictionary in Cisco ISE 2.3
After the import it should look something like below. Note that there are 10 defined VSAs but only the five first are used for authorization. The remaining five are used for Global Protect.
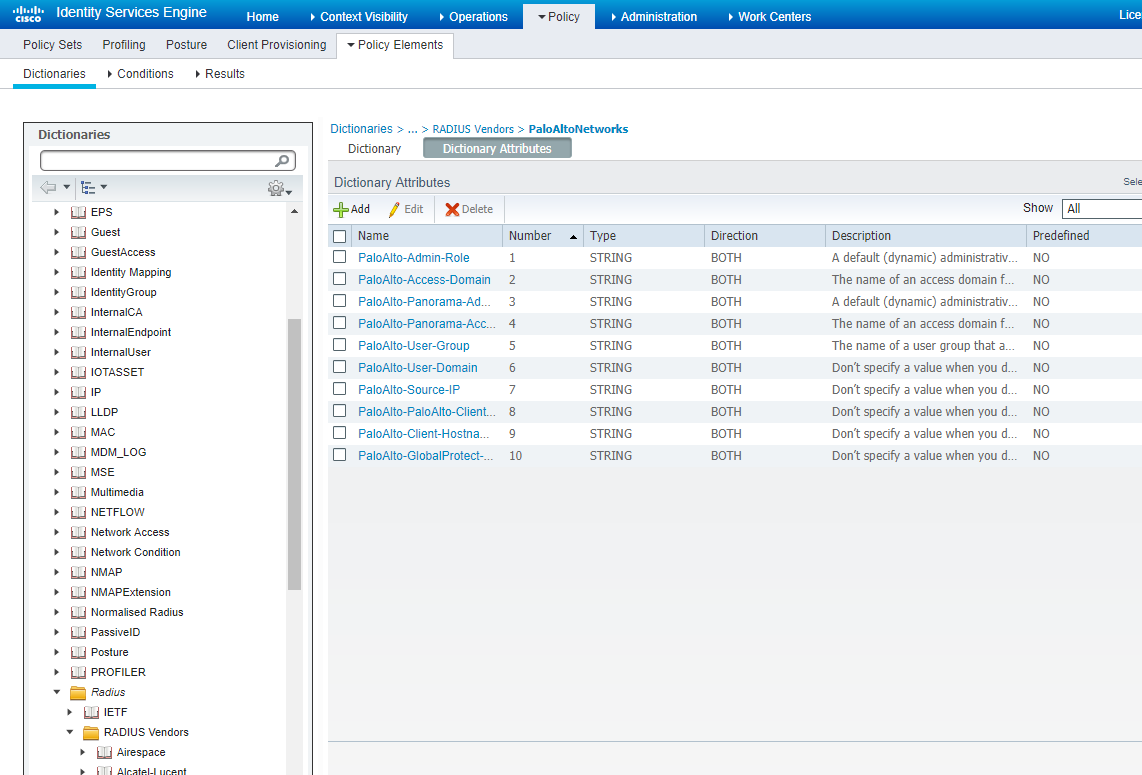
When imported it should look something like this
The next step is to add a new network device profile with a reference to the newly created dictionary.
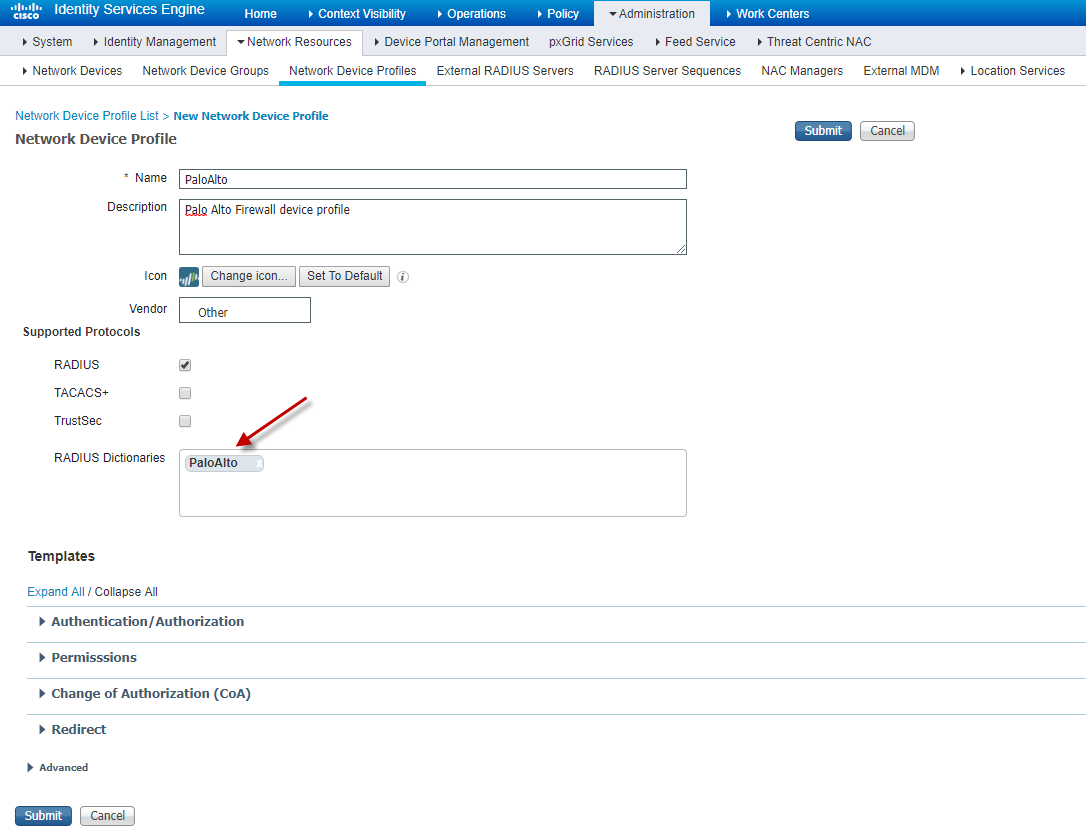
Create a new device profile as shown above or import this one (device-config-export).
The last step is to add the Firewalls to the list of network devices
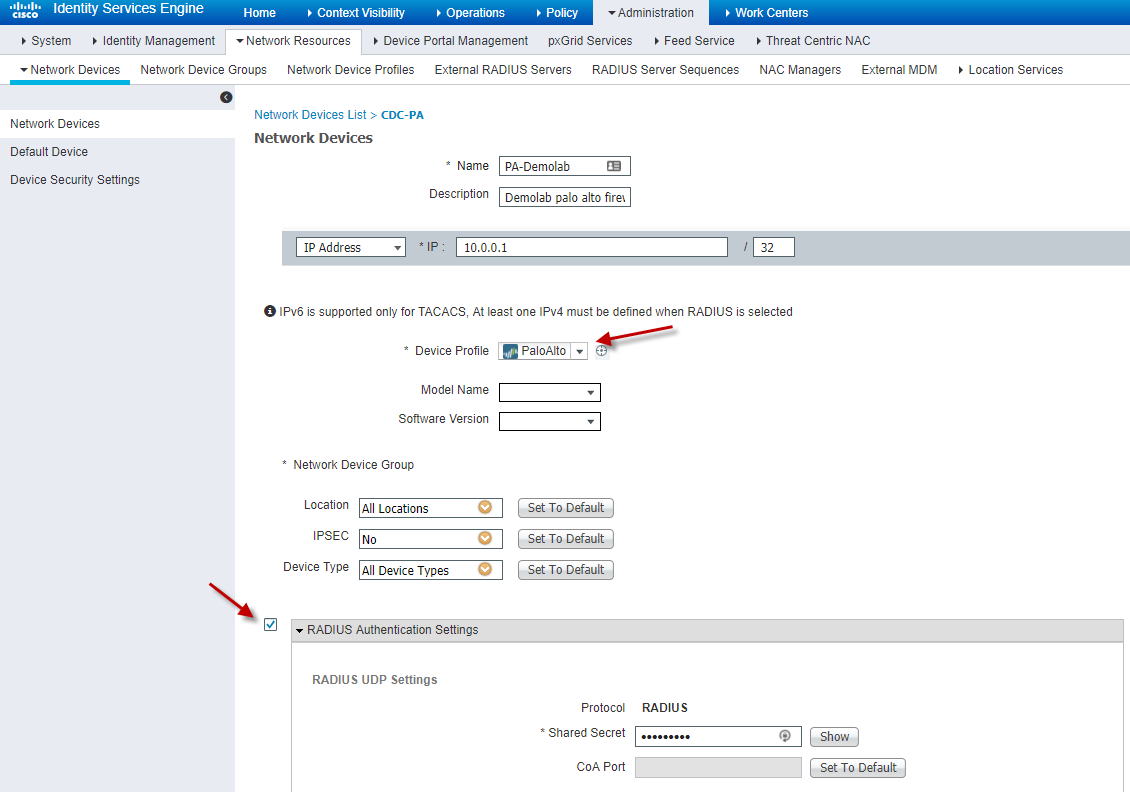
Adding the firewall as a network device in Cisco ISE
Then the needed authorization profiles can be made
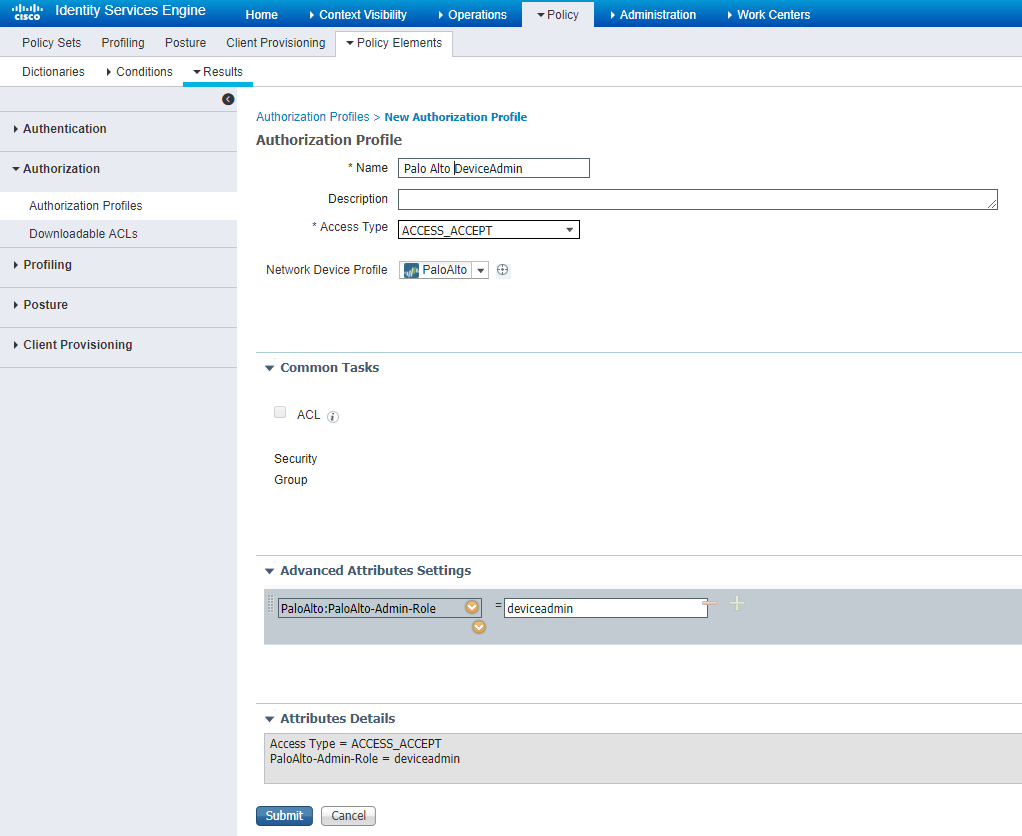
Create a authorization policy specifying the role on the Palo Alto Firewall
Values for the Admin-Role attribute (which is the most important one) are given in the table below:
# PaloAlto-Admin-Role is the name of the role for the user # it can be the name of a custom Admin role profile configured on the # PAN device or one of the following predefined roles # superuser : Superuser # superreader : Superuser (read-only) # deviceadmin : Device administrator # devicereader : Device administrator (read-only) # vsysadmin : Virtual system administrator # vsysreader : Virtual system administrator (read-only)
And lastly the authentication policies can be written in ISE as usual.
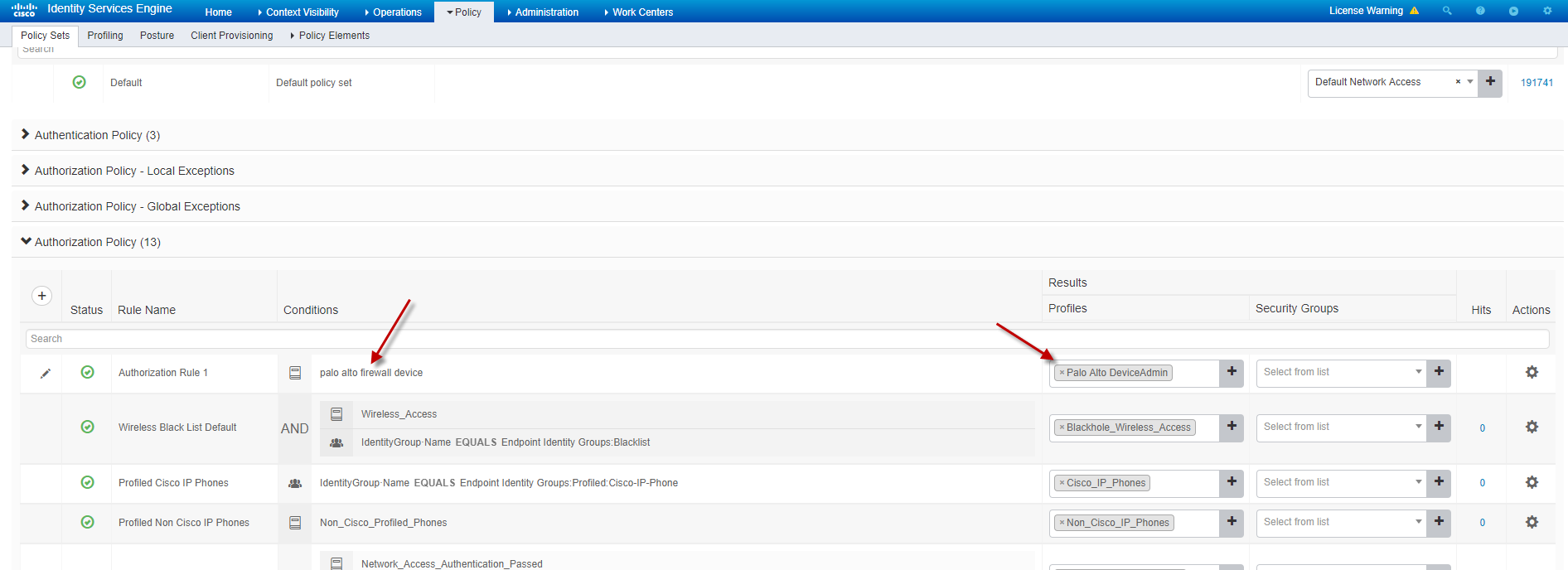
The simplest of policies … everyone authentication successfully from the Palo Alto firewall are granted the device-admin role
Setting up the Palo Alto Firewall
Only a few steps are required in order to set RADIUS validation up on the Palo Alto Firewall.
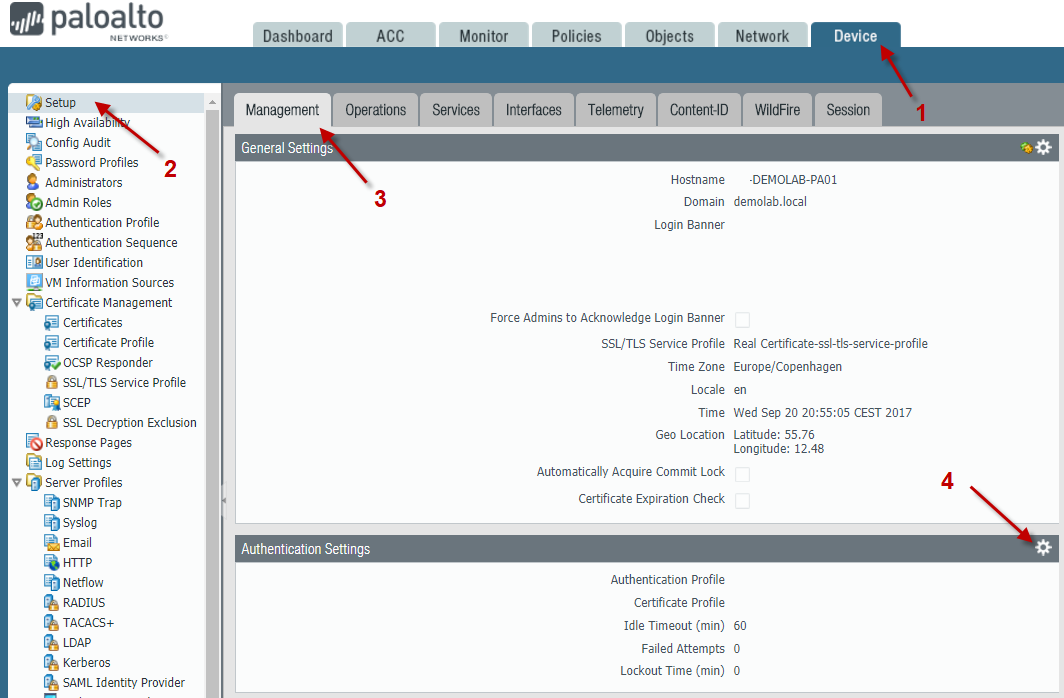
Navigate to the device tab
Pressing the configure button (4) will take you to a simple menu. Note again that only some authentication methods are supported here (this is due to the capability of role assignment).
Choose the the Authentication Profile containing the RADIUS server (the ISE server) and click OK. Commit the changes and all is in order.
Finally we are able to login using our validated credentials from Cisco ISE as well as having the privileges and roles specified in the Palo Alto Firewall but referenced through Cisco ISE.

Very bad. There is nothing about policy set , there is nothing about authentication policy. Can i use this guide in my work? NO.
I’m sorry you could not use the guide as written. It seems to always be a hard decision on how much to include in an article and how much background knowledge should be taken for granted.
I can highly recommend reviewing some of the basic ISE guides at http://www.network-node.com/blog/tag/ISE or perhaps sitting through a Ciscolive.com ISE presentation for the getting the basics covered.
I’d disagree with “Vasya”.
1. This guide is very helpful and intuitive
2. It can absolutely be used as a solid point of reference for Cisco+Palo mixed environments
3. It’s frustrating when individuals feel entitled by believing that everything should be spoon-fed to them.
One of the big problems in our industry as a whole, are people who don’t have the ability to be resourceful enough to fill in the blanks in relation to what they’re trying to accomplish in their custom environments. These individuals will not survive the dramatic shift to NetDevOps and SDN-based architectures.
Anyways, all of that to say: Great job Kristian. I appreciate this write-up very much.
whoah this weblog is wonderful i really like studying your articles.
Keep up the great work! You understand, lots of persons are looking round for this information, you could help them greatly.