I have had my hands on Ciscos new addition to their ASA firewall/IPS portfolio, the ‘Cisco ASA with Firepower Services’. And as with all technology there are both pros and cons to mention in this initial release (The current version is 5.3.1 and is following the firmware version of the old Sourcefire solution).
Cisco ASA with Firepower Services ‘ad’ from the datasheet
Cisco is not going to EoL their existing NGFW ASA CX module, however it is safe to say that it will no longer have any development priority (it is now referred to as NGFW gen. 1). Too bad since it only have had a few years of service, and that it was beginning to mature.
In short I think Ciscos new offering is primarily good! The somewhat longer answer is, that it depends a little on the installation size and the wanted functionality. And it does still strike me though as two separate products (Cisco ASA AND Firepower Services) because there is no uniform management platform. Apparently I’m to lazy to login to one place to do some rules, and another different place to do others. This is even though I’m on the same hardware platform (this is no different from the CX though).

The Sourcefire acquisition Cisco did a year (oct. 7, 2013) ago was certainly a good move. The old Cisco IPS engine (and also the newly integrated IPS part of CX) was perhaps leaving a little left to be desired while the Sourcefire is, or was, best-in-class. It is a grand feat. by Cisco to already have it integrated into their portfolio after only a years time!
The Firepower platform
The Cisco Firepower actually comes in two flavors:
One as a stand-alone appliance (HW or Virtual) which can do all the same stuff as a normal NGFW, with the exception of NAT, VPN, routing etc. The primarily use for the standalone will properly be as a sensor deeper within the infrastructure, rather than at the perimeter.
And then there is the ‘Cisco ASA with Firepower services’ which can do both. It is fair to consider the ASA and the Firepower services as two separate entities sharing the same power and network connections, though it of course is a somewhat crude generalization.
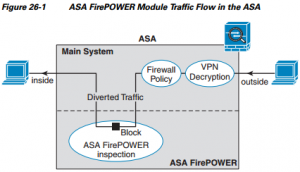
The ASA with Firepower services operates as either as a seperate HW module (for the 5585X series) or as an software component inside the ASA-X (all other models)
The ASA with Firepower services operates as either as a separate HW module (for the 5585X series) or as an software component inside the ASA-X (all other models). It functions the exact same way as the CX module, with a traffic redirection policy made in the ‘old’ ASA, with regard to which traffic is going to be inspected.
A slight note on the ASA with Firepower services is that it IS possible to change from CX on the non 5585-x, but the 5585-x IS NOT (require a new hardware blade).
Great analysis capability (though not on-box)
All Cisco Firepower services and appliances are managed and configured from an external server called Firesight (no local management can be done yet, but is rumored to be roadmapped). Cisco PRSM cannot be used for this purpose. Having an external management is both a very bad and a possible good thing. Its not very nice for smaller installations to have to manage an security infrastructure multiple places, and the fact that configuration and logs will be separated over two consoles is not convenient. However if the Firesight console is used with larger installations (multiple devices) or used to gain a high level of security insight it is actually pretty nice. The fact that is comes as dedicated server means that it has the processing power needed in order to crunch numbers and do retrospective analysis. The Firesight product originally comes from Sourcefire, so it is a good and very capable analytic tool. This retrospective analysis capabilities and the very good IPS functionality are in my view the strongest offering from the Firepower product at the moment.
The platform also maintains passive monitoring of the traffic beyond what is normally seen. Furthermore because of the available horsepower on the external management platform, it can actually correlate this into meanings full relations. Kudos to Sourcefires security analysis product.
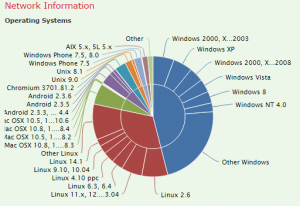
Firepower list of Host OS travelling the service. Screenshot from the Cisco Firesight manager.
Building of rules in the Firesight manager is pretty straightforward (intuitive) and pretty equal to whatever other NGFW vendor out there. Note specifically that the Firepower is Zone based (while the ASA is not). Zone based rulesets are great, and using Firepower it is now possible to make the ASA a pseudo zone based firewall.
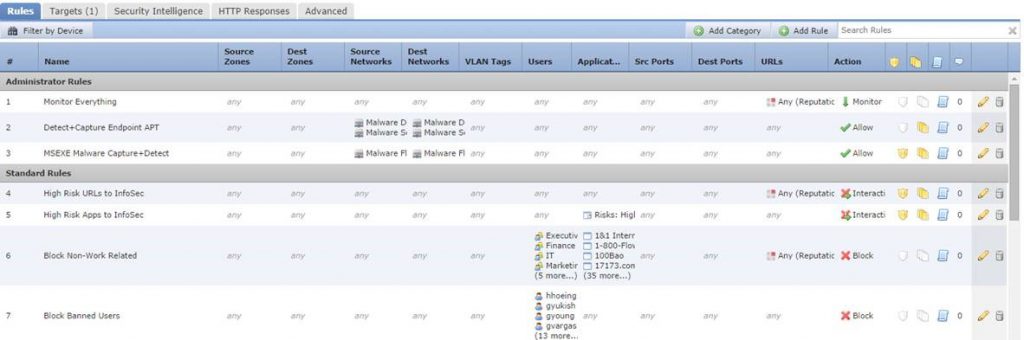
A screenshot from the Cisco Firesight manager in the rule building configuration. One thing to note though is that these rules ONLY applies to the traffic encompassed by the service-policy redirection in the original ASA ASDM/CLI
The detailed logs are also pretty good in the Firesight manager, but again they only contain the part which is redirected to the Firesight module, so if the entry you are looking for are not contained in this log, it might be in the ASA log.
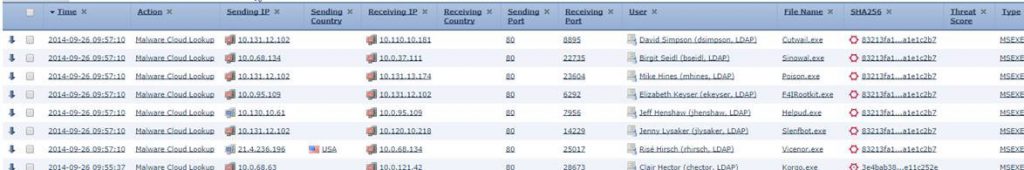
Firepower logs are rich but requires the right perspective and are not ‘unified’ with the ASA logs
A few hairs in the soup
Feature wise there are some things which has not (yet) made it to the Cisco Firepower:
- SSL decryption. This is extremely bad, as no hacker in their right mind would not utilize some sort of encryption. Actually it almost voids all the other good IPS engine. CX did have SSL decryption, so it is surprising that it did not made the cut to Firepower.
- No timebased rules. Some use them, while some don’t. It should be fairly simple to implement in a later release I guess.
- No QoS/shaping based on users/application. It can be argued that it is better set on the ingress of the network, but it is a missing feature compared to other vendors.
- I did not see any hint of active user identification, such as captive portals.
Performance?
A slight concern is the performance. Since all (interesting) traffic is being redirected to an ‘external’ module it comes with a performance penalty (as with most platforms and vendors). Ciscos sizing documents tell of performance degradation numbers of 30%-65% This of course just means that you needs to start high enough, when initial doing your spec:) . More over no one ever use as much bandwidth as they think… The datasheet also speak of these numbers
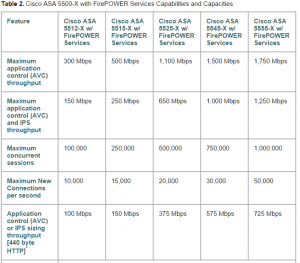
Figure from Cisco Firepower sizing document
Other new features
But again there is also a lot of new stuff compared to the CX module, each which could support an entire article: FireAMP (sandboxing technology), OpenAPP (open API for creating custom applications), Some very cool Cisco ISE integrations, SNORT IPS signatures, trajectory analysis and a lot more.
Conclusion
In summery; I think the Firepower is a very good security product. Especially the reporting and analytic parts. I do lack a better integration with the existing ASA and the performance drops when enabling features on the Firepower services scares me somewhat.
That said, Cisco is definitely on the right track with Firepower!
Be the first to comment on "Cisco ASA with Firepower Services"